Use Invisible Secrets to prevent unwanted people from reading your private files and communications
Invisible Secrets not only encrypts your data and files for safe keeping or for secure transfer across the net, it also hides them in places that on the surface appear totally innocent, such as picture or sound files, or web pages.
These types of files are a perfect disguise for sensitive information. Nobody, not even your wife, boss, or a hacker would realize that your important papers or letters are stored in your last holiday pictures, or that you use your personal web page to exchange messages or secret documents.
Invisible Secrets features: strong encryption algorithms; a password management solution that stores all your passwords securely and helps you create secure passwords; a shredder that helps you destroy beyond recovery
files, folders and internet traces; a locker that allows you to password protect certain applications; the ability to create self-decrypting packages and mail them to your friends or business partners; a tool that allows you to transfer a password securely over the internet and a cryptboard to help you use the program from Windows Explorer.
Invisible Secrets is shell integrated and offers a wizard that guides you through all the necessary steps needed to protect your data .
Here are some key features of "Invisible Secrets":
· Invisible Secrets is an easy-to-use yet a powerful wizard-interfaced cryptography/steganography program.
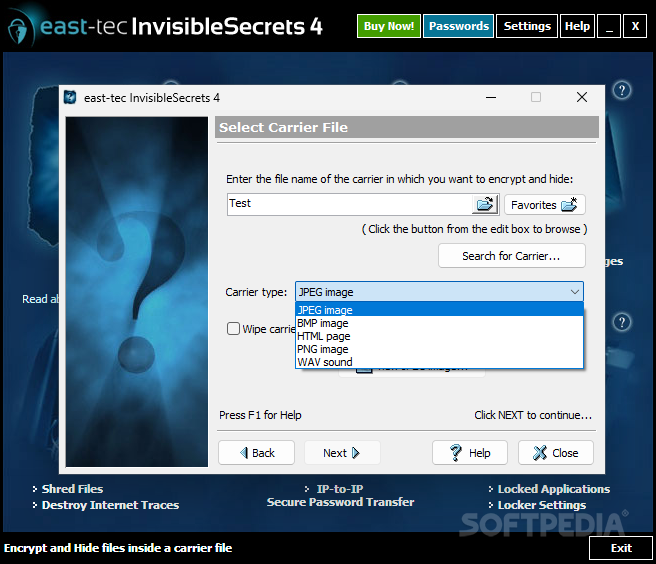
· Five Carriers: JPG, PNG, HTML (without any data length restriction), BMP and WAV (source data proportional with the size of the image/sound).
· Strong cryptography: AES-Rijndael, Blowfish, Twofish, RC4(TM), Cast128, GOST, Diamond 2, Sapphire II.
· New! create self-decrypting files
· It includes a shredder which conforms to the norm of the US Department of Defense DoD 5220.22-M
· New! wipes out internet traces
· It includes a Password Manager
· New! IP-to-IP password transfer
· Shell integration (The "Invisible Secrets" submenu appears in the system context menu)
· New! Functions available through the Tray Icon
· New! Cryptboard
· New! Application Locker
· It is also very flexible: The user can develop his own algorithms or carriers and integrate them very easy in the program
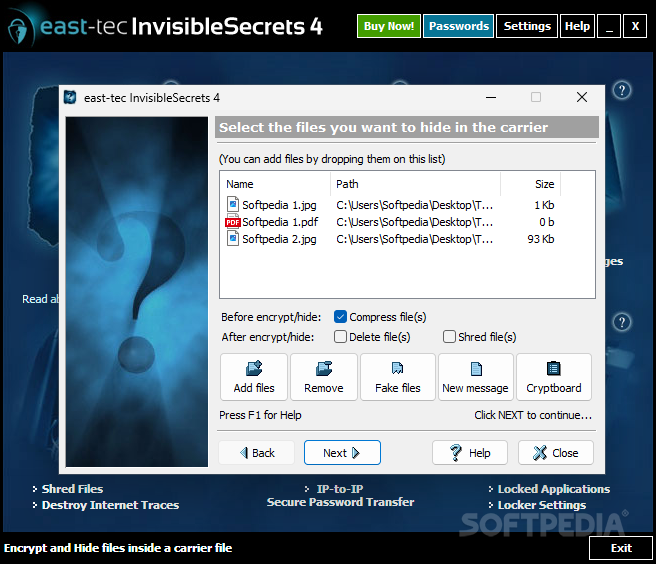
· Data compression before the encrypt/hide process
· Mail the resulted carrier after the process or place it somewhere on the Internet through a FTP Connection.
· A very well organized FTP Servers Library
· Secured algorithms and carriers libraries through activation keys
· Fake messages generator.
· Perfect local security: all the temporary files used in the process are wiped out
· The possibility to wipe the source data or the original carrier after the process
· Invisible Secrets uses a complex shredding method (DoD compliant): seven pass wiping with randomly generated patterns which makes hardware recovery impossible.